Why Business Email Compromise Is Your Company’s Biggest Blind Spot
I’m about to tell you something that might save your company from financial ruin. And no, this isn’t some hyped-up sales pitch about the latest software gizmo.
This is about a sophisticated threat that’s draining business bank accounts while everyone’s distracted by ransomware headlines.
It’s called Business Email Compromise (BEC). And if you’re not specifically defending against it, you’re leaving your company’s finances exposed.
The New Economics of Cybercrime
Smart criminals follow the money. And right now, the money is in BEC scams.
Why? Simple economics:
- Lower risk than ransomware (no messy encryption)
- Higher success rate (exploits human trust, not technical weaknesses)
- Bigger payoffs (some attacks net hundreds of thousands)
- Almost impossible to trace or recover
While everyone’s focused on preventing ransomware, these criminals are quietly targeting corporate bank accounts through carefully crafted emails.
The Anatomy of a Modern BEC Attack
Here’s what makes these attacks so dangerous:
They’re not random. They’re surgical strikes based on intelligence gathering.
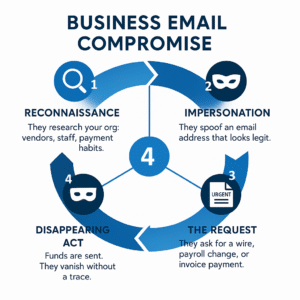
Phase 1: Reconnaissance
Criminals spend weeks inside your email system, learning:
How your executives communicate
Your payment processes
Your vendor relationships
Your typical transaction amounts
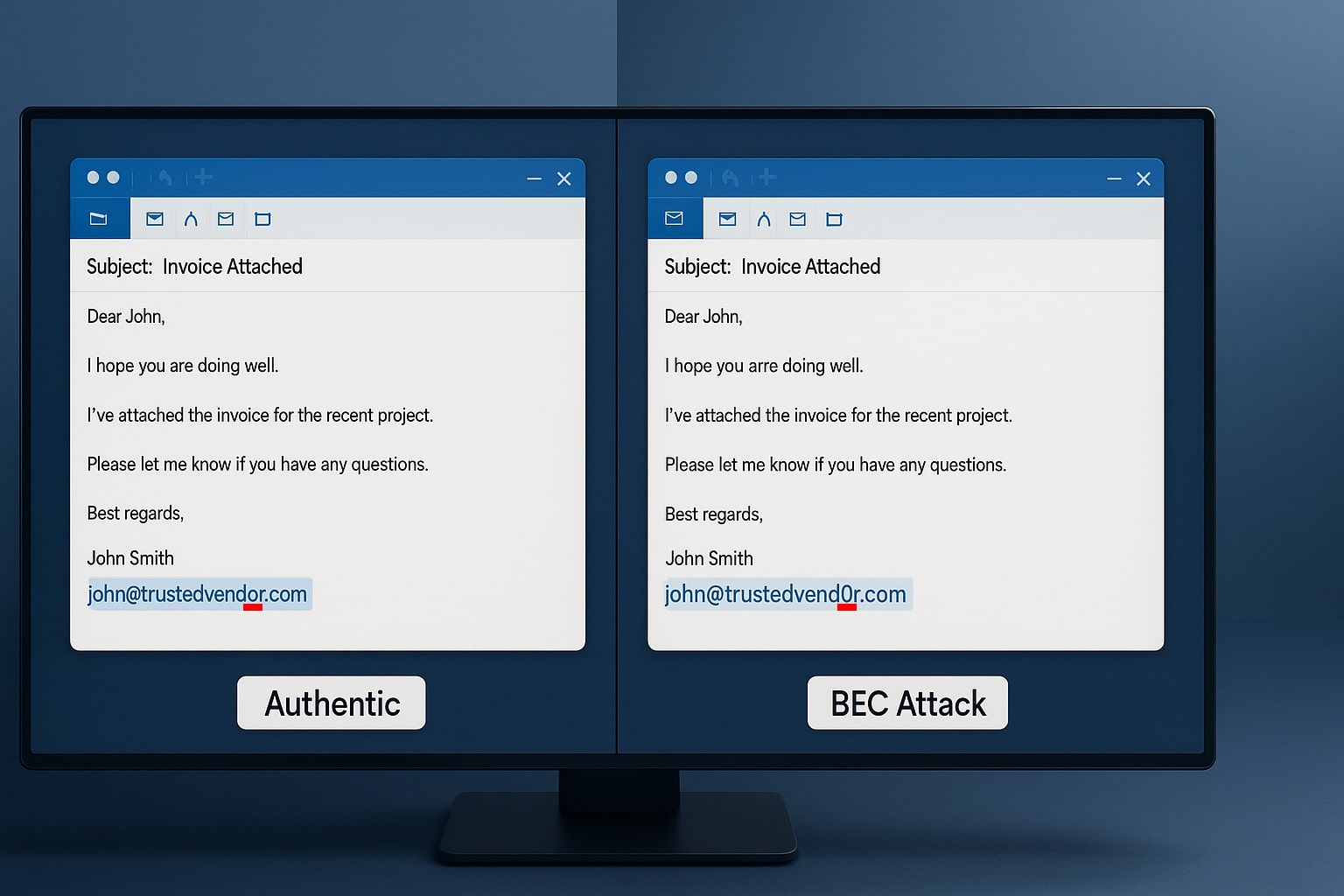
Phase 2: The Perfect Impersonation
They create near-identical email addresses. They match writing styles. They reference real projects and relationships.
Phase 3: The Logical Request
The fake email always makes business sense:
“Wire funds for the acquisition we discussed”
“Update our payment details in your system”
“Process this invoice before month-end close”
Phase 4: The Disappearing Act
Money transfers through multiple accounts across several countries within hours. Recovery is rarely possible.
Why Traditional Security Fails
Your current cybersecurity likely has three critical gaps:
- The Human Factor: Your employees want to be responsive. BEC exploits this.
- The Authentication Gap: Email wasn’t designed for financial transactions.
- The Training Deficit: Most security training doesn’t address sophisticated social engineering.
The Strategic Solution
At Blue Light IT, we’ve developed a comprehensive BEC defense strategy that addresses all three gaps:
1. Advanced Email Intelligence
AI-powered analysis of communication patterns
Real-time detection of impersonation attempts
Automatic flagging of unusual requests
2. Process Integration
Verification protocols that don’t slow business
Clear escalation procedures for suspicious requests
Integration with your existing workflow
3. Human Firewall Development
Scenario-based training using real BEC examples
Regular testing with simulated attacks
Continuous reinforcement of security habits
The Real Cost of Being Unprepared
Consider what’s at stake:
Direct financial losses from successful attacks
Reputation damage with clients and partners
Operational disruption during incident response
Potential legal and compliance issues
Our clients tell us their biggest fear isn’t the technology failing—it’s their own team being tricked by a convincing email.
Your Next Strategic Move
Every day without proper BEC protection is another day of unnecessary risk. But you don’t have to figure this out alone.
We offer a complimentary BEC Vulnerability Assessment that will:
Identify your specific vulnerabilities
Map your current email security gaps
Provide a customized protection roadmap
Show you exactly how to implement verification protocols
This isn’t about selling you software. It’s about architecting a defense strategy that fits your business operations.
Take Action Now
Book a 20-minute consultation with our security strategists. We’ll show you:
Your company’s specific BEC risk profile
Which quick wins can immediately reduce your exposure
How to implement protection without disrupting operations
The exact steps to turn your team into security assets
Don’t wait for that expensive email to arrive. Protect your business now.
Remember: In cybersecurity, the best time to implement protection was yesterday. The second-best time is now.