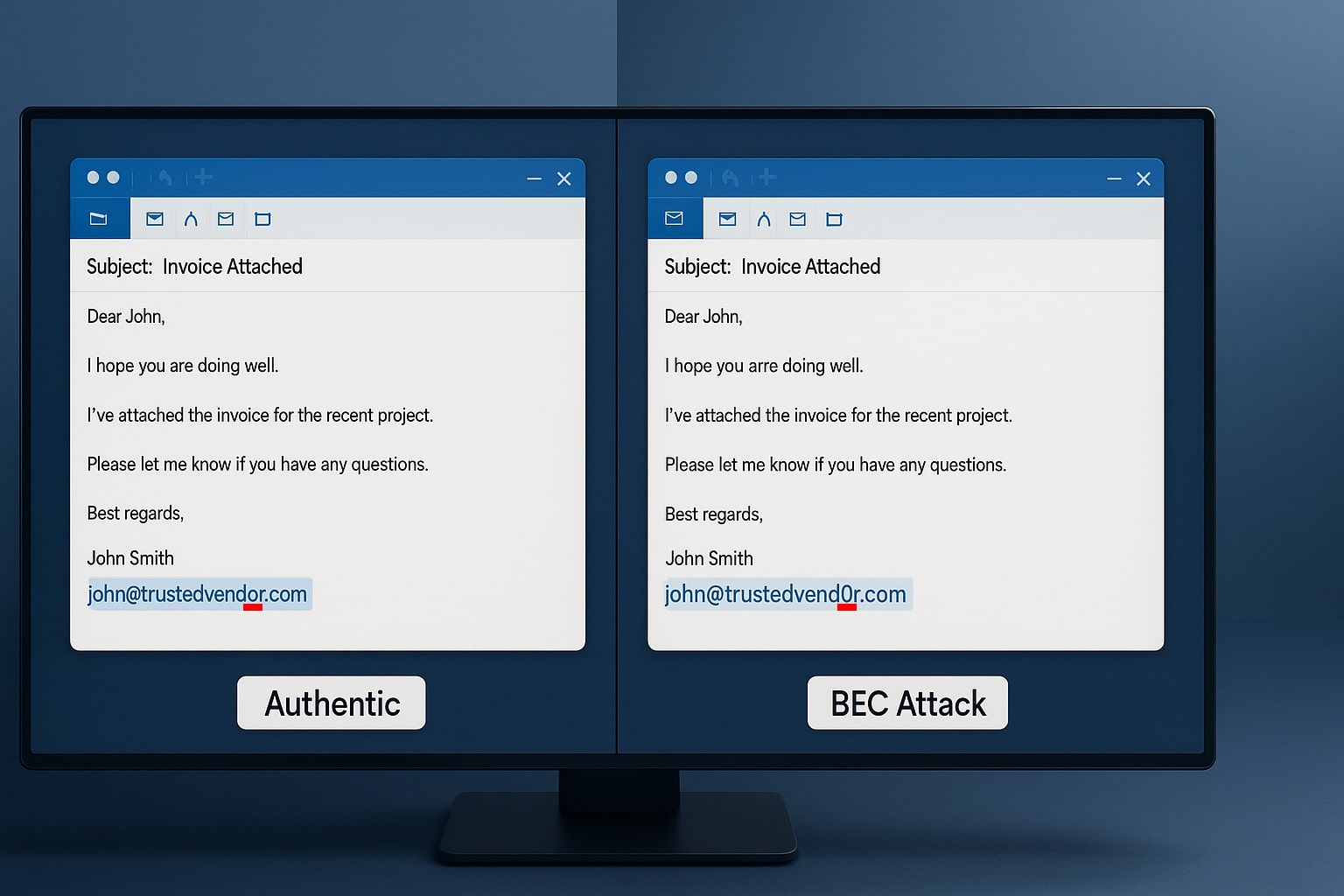
Can I Take a DIY Approach to the FTC Safeguards Rule?
Does Your Firm Have The Right Cyber Security Program?
If you’re a tax preparer dealing in personally identifiable information (PII), you’ve likely seen articles related to the newly updated FTC Safeguards Rule.1
The rule will take effect soon, specifying that “financial institutions [must] develop, implement and maintain an information security program with administrative, technical and physical safeguards designed to protect customer information.”You must implement a cyber security program to protect your clients’ data. The rule denotes explicitly nine tenants to follow under the law.
We’ve interviewed Amir Sachs, CEO of Blue Light IT and bestselling author of cyber security guides, to help explain in more detail what you can do as an individual to implement an FTC Safeguards Rule-compliant cyber security program.
Need to Be Sure Your Business is Compliant with The New Requirements?
Is it possible to take a DIY approach to comply with the new requirements of the FTC Safeguards Rule?
“Yes and no: There are nine steps for the FTC Safeguards Rule. The first one is to appoint a qualified person, anyone can be qualified to do that, the only requirement is the person needs to be familiar with real-world know-how of how information is stored and processed in the business. They don’t need to be experts, they don’t need to have any college degrees. If the person knows how and where information is stored, they can become the qualified person.”
How do I know that I’ve appointed or outsourced to the right individual?
“If you are appointing internally, all they need to know is how you store and process data. If you’re appointing externally, then you should appoint somebody that displays knowledge about cyber security and takes interest in your business other than just getting their bill padded at the end of the month. This is an ongoing engagement, this is not a one-off engagement.”
What is involved in a risk assessment, and can I do it myself?
“A risk assessment has two portions: an interview section and a technical analysis. We discover the current security position of the company, we establish a baseline of where they are at the moment and identify high-risk security flaws, which offer easy access to hackers.
The questions we ask help us understand the risk to the business operation, and we estimate the financial impact of a security breach. The CSRA (cyber security risk assessment) is designed to investigate the existing business practices, test staff readiness and analyze business technology infrastructure to determine whether the people, processes and technology are aligned to repel cyber attacks and aligned internally with what they need to do.
The results will give management of the company the facts regarding their business so ownership can make an informed decision regarding next steps.”
The risk assessment is designed to accomplish three goals:
- Determine the state of the existing cyber security and information security processes and any best practices within the organization.
- Identify any existing security gaps.
- Provide the executive team with a current picture of the organization’s ability and readiness to withstand a cyber attack.
“The report that they get at the end of the assessment will highlight any gaps they have in their security and provide steps to remediate. They could take those steps and provide them to any IT company that does cyber security and the IT company will be able to implement and close the gaps. The technical analysis is done remotely.
The risk assessment is optional if the company is small and has less than 5,000 consumer records. Anyone who would go for a do-it-yourself approach is probably not going to have more than 5,000 users and therefore they are exempt. If they have more than 5,000, they should not be doing it themselves.”
Need to Be Sure Your Business is Compliant with The New Requirements?
Next Steps
If you’d like to learn more about the rest of the tenants of the FTC Safeguards Rule, come to our free educational webinar on January 19, 2023 at 11 AM Eastern. And, if you have any questions related to cyber security or would like to schedule a risk assessment, contact us or book a meeting.
Entrust your business to a team of reliable and responsive experts: You won’t regret it.
- https://www.ftc.gov/business-guidance/resources/ftc-safeguards-rule-what-your-business-needs-know
Related Posts

Law Firms Beware: The Silent Ransom Group is Calling
read more
Slopsquatting: The AI Security Threat Every Development Team Must Address
read more