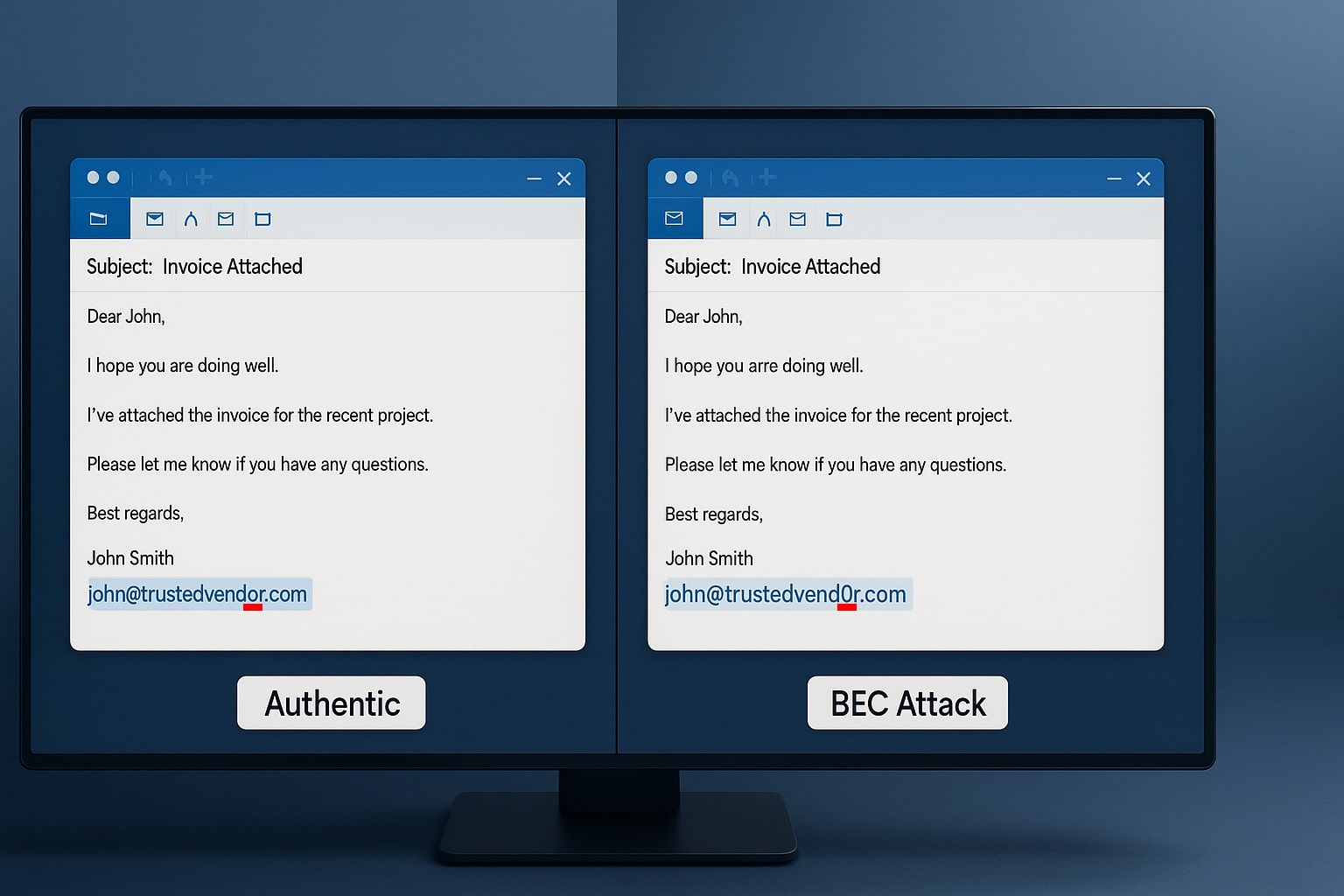
The FTC Safeguards Rule may be completely new to you or maybe you have some familiarity. Either way, you probably have questions and are wondering what you need to know. Here are a few answers to frequent questions.
What is the FTC Safeguards Rule?
The FTC Safeguards Rule “requires covered financial institutions to develop, implement and maintain an information security program with administrative, technical and physical safeguards designed to protect customer information.”
In other words, you must implement cyber security plans to protect client data, with a looming deadline of mid-2023. Failure to do so may result in an FTC investigation. Learn how to comply with these rules and read more guidance on data security in IRS Publication 4557, Safeguarding Taxpayer Data.
Need to Learn More about Industry Trends and Compliance?
When will the rule take effect?
On June 9, 2023, the FTC will start enforcing the Safeguards Rule to ensure that entities covered by the rule maintain safeguards to protect the security of customer information.
The FTC notes that even if your business wasn’t covered by the original version of the rule, your business operations have likely evolved and changed over the past 20 years. Your business as it stands today may meet the current definition of a financial institution.
All companies interact with personally identifiable information, so understanding these new requirements is critical.
What are the new requirements?
There are nine new requirements outlined in the FTC Safeguards Rule that affected organizations must comply with:
1. Appoint a Qualified Individual
Your company needs to appoint a “qualified individual” who will implement and supervise your information security program. It can be someone who works for you or an outside person. No particular degree is required. The person needs to be familiar with your “real world” operations of how you store and process information in the business.
2. Perform a Risk Assessment*
To formulate and execute an effective information security program, you need to know what information you have and how/where it is stored. The risk assessment should look at both internal and external security factors as well as the confidentiality and integrity of your customers’ information.
*If you hold financial information for fewer than 5,000 consumers, you are not obligated to perform a risk assessment.
3. Design and Implement Safeguards to Control Risks
This process involves eight steps, outlined below:
- Maintain and regularly review access controls to the data.
- Periodically conduct an inventory of where your data is collected, stored and transmitted. Record this discovery regularly.
- Encrypt customer information on your computer systems and while sending it to others (at rest and in transit).
- Evaluate the apps you use that store customer data.
- Set up multi-factor authentication for any system that could potentially have customer data (email, file system, cloud storage, etc.).
- Permanently delete customer information after two years, unless you have a legitimate or legal need to keep it in your files.
- Plan for any changes to your information system or computer network. The plan should always include security first.
- Keep a log of any user activity when accessing customer data and implement policies and procedures of what to do should you notice unauthorized access to customer data.
4. Test Your Safeguard Plan Regularly
This can be achieved either by continuously monitoring your environment or by conducting a penetration testing and vulnerability assessment every six months.
5. Train Your Employees
Provide all your employees with continuous security awareness training.
6. Monitor Your Vendors and Service Providers
Any service provider who may have access to your customer data should have the skills and experience to maintain the same level of safeguards as if they were your employee.
7. Keep Your Information Security Program Up to Date
You should re-evaluate your security program whenever you experience a change in your business (replacing employees, changing software vendors, adding staff, etc.)
8. Have a Written Incident Response (IR) Plan*
Have you ever experienced a fire drill? An IR plan is like a written version of a fire drill. This document will outline the steps you need to take should you have a security event.
*If you hold financial information for fewer than 5,000 consumers, you are not obligated to keep an IR plan.
9. Have the Qualified Individual Report to Your Board of Directors*
Regardless of whether your qualified individual is on your staff or is an outsourced entity, that role needs to submit regular annual reporting to your board of directors or governing body.
*If your company doesn’t have a board or governing body, the report should go to a senior person (usually the owner of the company.)
Need to Learn More about Industry Trends and Compliance?
This sounds like a lot of work. What if I don’t comply?
You could take the easy route and ignore the new requirements, but it could ultimately endanger your company. Here’s what could happen if your company experiences a data breach, according to the FTC:
- Expensive fines. The maximum fine you can incur from a data breach is $11,000 per day. The agency can also seek damages for consent violations which could total over $43,000 per day for each violation, as well as possible jail time.
- Extensive penalties. Your company could face long-term consent decrees or extensive injunctive relief, which could significantly stifle your business operations.
- Litigation risks. Your company could be sued in case of a security breach. Cases where you have to notify victims after a breach significantly increase the risk of litigation.
- Reputational damage. The ripple effect of a security breach cannot be underestimated. Not only will it impact your customers’ trust, but it will also negatively affect your relationships with other affiliates and suppliers.
- Data loss. Your data is more valuable than you think. The average data breach in the United States costs $9.44 million, over $5 million more than the global average.
Need to Learn More about Industry Trends and Compliance?
Next Steps for the FTC Safeguards Rule
If you’re worried about the new FTC Safeguards Rule and how it will affect your company, we can help.
Click here to Book a meeting with us to schedule a risk assessment, or contact us with any questions you may have about the FTC Safeguards Rule or any other IT concerns.
Entrust your business to a team of reliable and responsive experts: You won’t regret it.
Related Posts

Law Firms Beware: The Silent Ransom Group is Calling
read more
Slopsquatting: The AI Security Threat Every Development Team Must Address
read more