As organizations increasingly rely on technology for their daily operations, the potential for malicious actors to exploit vulnerabilities in digital systems has surged dramatically. Understanding how cyber-attacks occur and learning how to effectively respond is essential in safeguarding our sensitive information and preserving the integrity of our critical infrastructure.
Below, we’ll delve into the intricate world of cyber-attacks and explore their various forms, motivations behind them, and most importantly, we’ll equip you with practical strategies to mitigate risks and respond effectively when an attack occurs. It’s time to unravel the intricacies of cybersecurity and empower ourselves with the tools needed to combat these ever-looming threats head-on.
Below, learn about common cyberattacks that occur and how to prepare for them with proper cybersecurity measures and Boynton Beach business continuity planning.
Need to Learn More How to Keep Your Business Protected?
Understanding Common Cyber Threats
Cyber-attacks can manifest in various forms, including malware, phishing emails, ransomware, and denial of service (DoS) attacks.
To effectively respond to cyber-attacks, organizations must adopt proactive measures such as regular system updates and patching vulnerabilities promptly. Strong security practices include employing firewalls, antivirus software, and robust password management protocols.
Educating employees about the risks associated with clicking on suspicious links or downloading unknown attachments is also essential.
Understanding common cyber threats empowers individuals and organizations to protect themselves against potential breaches of their sensitive information and infrastructure.
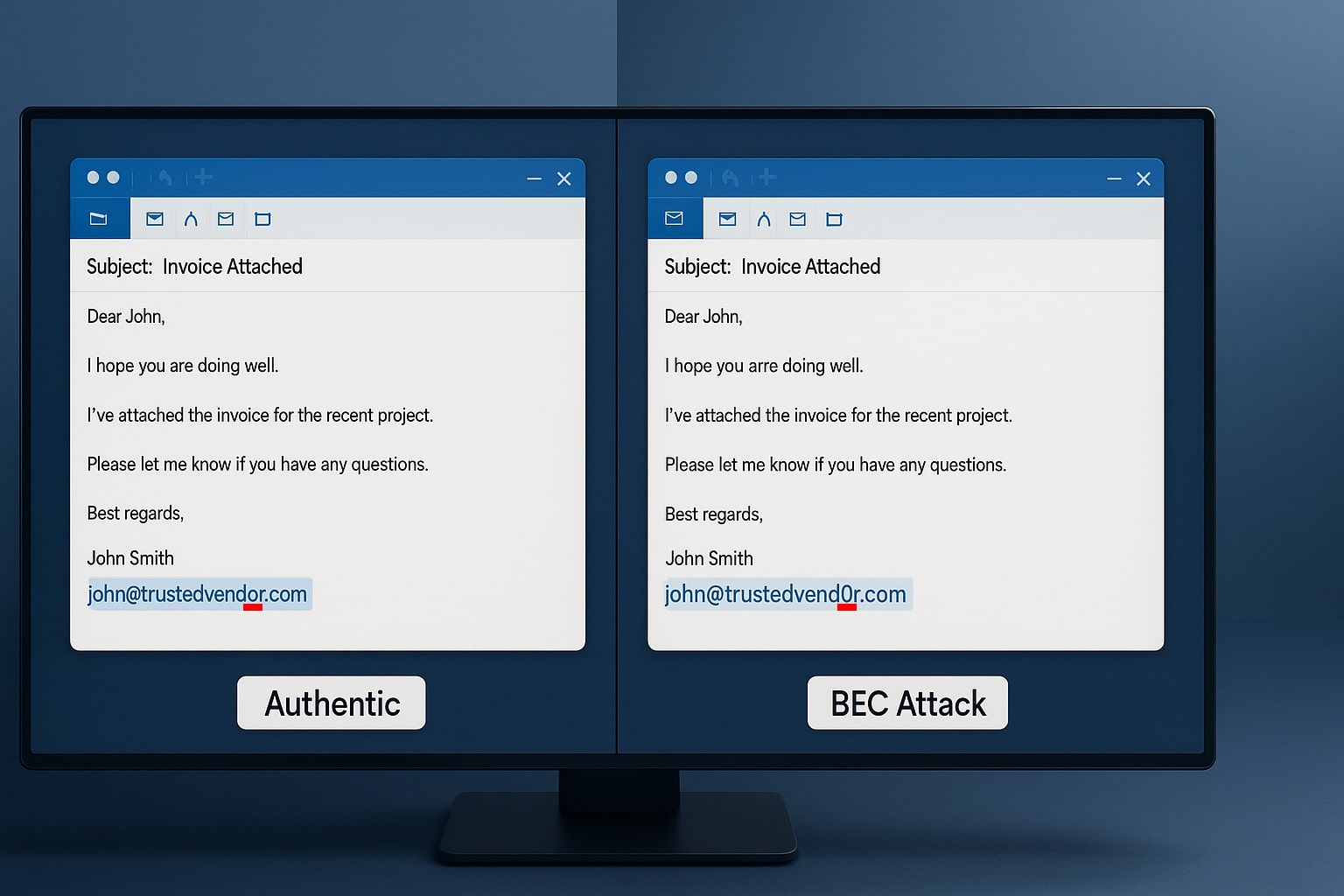
Phishing Scams
Phishing scams are a common method used by cybercriminals to trick individuals into divulging sensitive information and gaining unauthorized access to their personal or financial accounts. These scams typically involve the fraudulent use of emails, messages, or websites that masquerade as reputable organizations or individuals.
Phishers often employ sophisticated tactics such as creating convincing replicas of legitimate websites, using social engineering techniques to manipulate victims into sharing their login credentials, credit card numbers, or other confidential data.
One of the most alarming aspects of phishing scams is their ability to deceive even tech-savvy users. Cybercriminals continually refine their methods to make phishing attempts more convincing and harder to detect.
They may personalize messages with credible logos and branding, use urgent language designed to instill panic or urgency in recipients, or craft messages tailored specifically for a particular target group.
To protect ourselves from falling victim to phishing attacks, it’s essential to remain vigilant when interacting with electronic communications. Some key steps include verifying the legitimacy of emails before clicking on any links or downloading attachments; avoiding providing personal information over unsolicited email requests; cross-referencing URLs with official website addresses; and maintaining up-to-date antivirus software and firewalls on all devices.
Malware Attacks
Malware attacks are one of the most common and damaging forms of cyber-attacks. Malicious software, or malware, is designed to infiltrate computer systems without the user’s consent or knowledge.
Once installed, malware can carry out a variety of harmful activities such as stealing sensitive information, disrupting system functions, or even taking control of the entire system.
There are several ways in which malware can be delivered to a target device or network. One common method is through phishing emails that trick users into clicking on malicious links or downloading infected attachments. Another method is through drive-by downloads, where attackers exploit vulnerable websites to automatically install malware onto visitors’ computers.
To mitigate the risk of these attacks, it’s important for individuals and organizations to implement strong cybersecurity measures such as regularly updating software patches, using up-to-date antivirus programs, and educating employees about potential threats like phishing attempts.
Need to Learn More How to Keep Your Business Protected?
Ransomware Attacks
Ransomware attacks involves hackers infiltrating a computer system, encrypting critical data, and demanding a ransom for its release. The impact of ransomware attacks can be devastating, paralyzing entire organizations and causing significant financial losses.
Typically, ransomware enters a system through email attachments or malicious links that unsuspecting users click on. Once inside the network, it quickly spreads across systems and begins encrypting files. Victims are then presented with instructions on how to pay the ransom in order to regain access to their data.
Responding effectively to a ransomware attack is crucial for minimizing damage and preventing further spread. Organizations should prioritize incident response plans that include regular backups of critical data stored offline or in cloud-based solutions protected by multi-factor authentication.
Timely detection and isolation of infected systems are also essential steps towards containing the threat and mitigating potential losses.
Tips for Combatting Cyber Attacks
Combatting cyber-attacks requires proactive measures such as continuously updating security systems and employing encryption protocols. By staying ahead of potential threats through regular assessments and testing, organizations can identify weaknesses before they become exploitable entry points for attackers.
Implementing strong authentication processes and ensuring employees are well-trained in cybersecurity best practices can greatly reduce the risk of unauthorized access or data breaches.
Responding effectively to a cyber-attack also includes swift incident response protocols such as isolating affected systems, preserving evidence for forensic analysis, notifying relevant stakeholders about the breach, and coordinating with law enforcement agencies if necessary.
It’s vital that organizations have detailed plans in place that outline step-by-step procedures for handling different types of threats so that everyone knows their roles and responsibilities during an emergency situation.
Educating Employees on Cybersecurity
One way to educate employees is through comprehensive training programs that cover various aspects of cybersecurity. These programs should focus not only on identifying common cyber threats, such as phishing emails or malware, but also emphasize the importance of strong passwords, regular software updates, and best practices for staying safe on the internet.
Employees should be educated about the potential consequences of a cyber-attack, including financial loss, data breaches, reputational damage, and legal implications.
Due to the increasing reliance on technology in daily operations, taking steps toward educating employees about cybersecurity has become more important than ever. This includes providing comprehensive training programs that cover all key areas – from identifying common threats to implementing secure internet practices. Employees need to understand the consequences associated with becoming victims.
With this thorough education process, stakeholders are likely to reduce their susceptibility towards falling victim to breach attempts while further protecting sensitive information at a massive scale.
Need to Learn More How to Keep Your Business Protected?
Staying Safe With Boynton Beach Cybersecurity Solutions
It’s crucial for your business and employees to stay updated on the latest cybersecurity threats and best practices in order to minimize vulnerability. This involves regularly updating software and security systems, utilizing protection software (such as firewalls and antivirus solutions), employing strong passwords and encryption methods, and providing education and training on cybersecurity awareness.
It’s also essential to have a robust incident response plan in place that outlines clear steps to be taken in the event of a cyber-attack. Swiftly detecting an intrusion or breach and taking action can significantly limit the damage caused by hackers.
Safeguarding our sensitive information and critical infrastructure from cyber-attacks requires ongoing vigilance and adaptability to threats that are rapidly evolving. By implementing effective preventive measures and having strong incident response strategies in place, we can stay protected as cybercriminals become more sophisticated.
If you’re looking for disaster remediation in Boynton Beach, or anywhere in South Florida, contact Blue Light IT today to learn how we can help your company.
Related Posts

Law Firms Beware: The Silent Ransom Group is Calling
read more
Slopsquatting: The AI Security Threat Every Development Team Must Address
read more