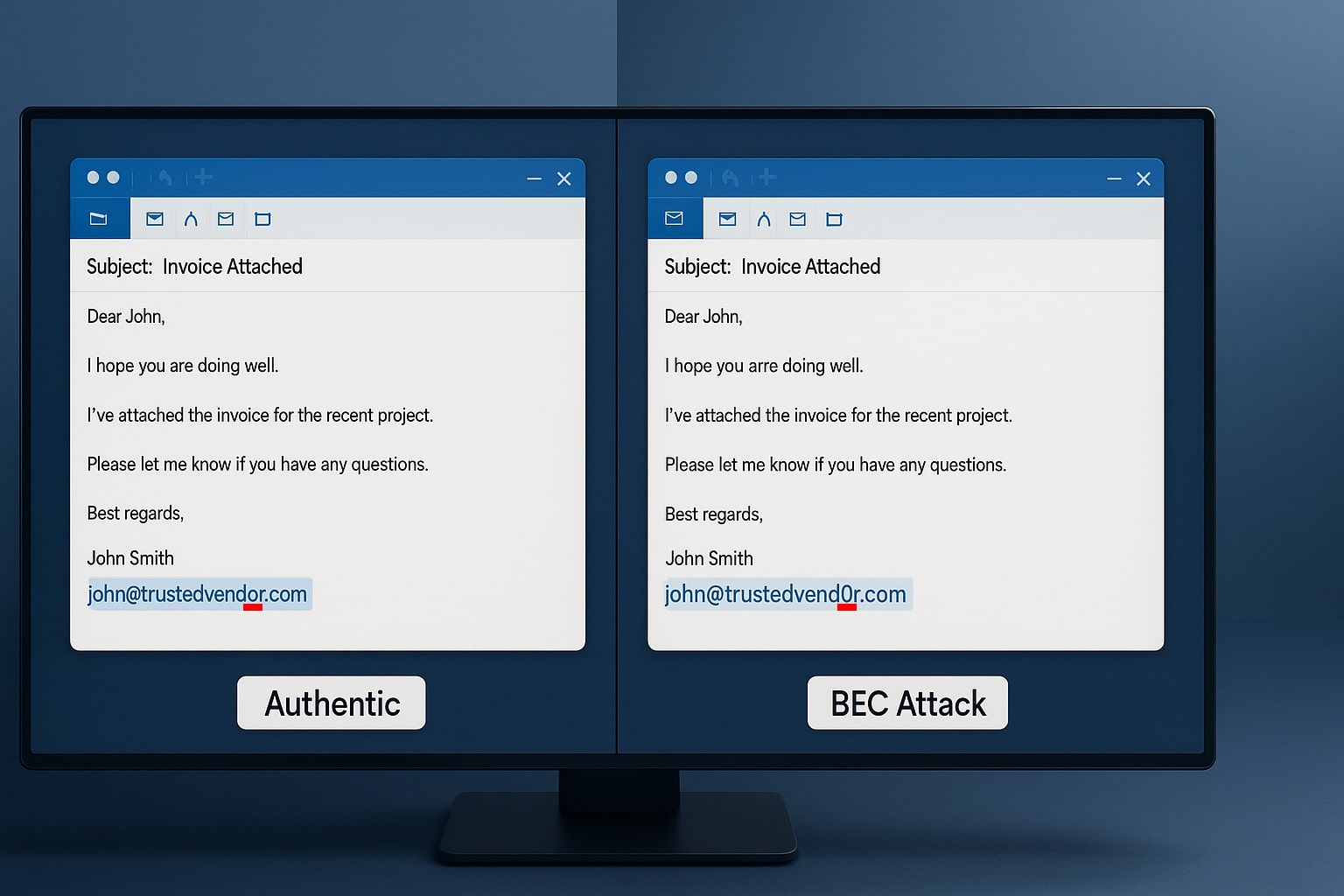
Endpoint protection is an important service that organizations rely on to keep their computer systems and networks safe from significant loss. While some companies may use endpoint security as a preventative measure, others choose to hunt down malware that has already taken root in their computer system.
Need to Keep Your Business Protected?
What is an endpoint?
An endpoint is a physical device that connects to a network. Using the endpoint suggests that the system connected to it could be a desktop, server, or laptop computer. Endpoints may also be mobile devices such as PDAs, smartphones, and tablets. Most of these devices use Microsoft, Apple, or Linux operating systems.
The endpoint includes every device that’s a part of a network or even standalone computers or devices that have been connected to one in some way. Every device that connects to a network, be it a desktop, laptop, or smartphone.
The endpoint is the “gateway to the network,” a point of entry into each network from which one may access other devices, systems, and information.
How does endpoint protection work?
Endpoint protection is involved in preventing, detecting, and recovering from malware. This process is generally automated and involves the use of the software. Endpoint protection has eight major features which define how it works:
Machine Learning
Machine learning is the primary method used by endpoint protection to identify new or unknown threats. Machine learning is an artificial intelligence technique that uses data analysis software to make predictions about unknown patterns in information. This software will be able to decide how to classify a computer system as malicious or safe based on its behavior.
Behavioral Analysis
Behavioral analysis is the second method used by endpoint protection to identify new or unknown threats. The behavioral analysis software monitors all the system’s activity, including keystrokes and other actions performed on the operating system and applications. This helps the software identify if any unsafe or malicious activities are taking place on the computer system. Malicious behavior in a computer that is being monitored will be flagged by behavioral analysis monitoring software.
Known Attack Detection
Known attack detection is the third method used by endpoint protection to identify new or unknown threats. This involves comparing current and historical data on the operating system and software applications to determine if there has been any change in terms of malware or other malicious applications.
Need to Keep Your Business Protected?
Exploit Mitigation
Exploit mitigation involves using exploit mitigation software that executes a program in a sandbox to detect if it contains any existing or new vulnerabilities that can be taken advantage of.
Cloud-Based Centralized Management
Cloud-based centralized management involves using centralized management software that does not require any system to be installed to handle the required security features of endpoint protection. This can be done from any device and from anywhere in the world. The centralized software is accessed through the Internet, allowing users to access their devices.
Automation
Automation has been included in endpoint protection to minimize the possibility of human error in carrying out security procedures. This is done by completing various tasks automatically, from installation to updating the operating system and application software.
Single- Agent Architecture
The single-agent architecture has been included in endpoint protection to simplify installing, updating, and removing software from one computer system to another. This is done using a single software that works with different operating systems to provide system-wide protection.
Remediation
Remediation has been included in endpoint protection to restore a computer system to its original state after malware or other malicious applications have been removed. This is done using a single software to scan the entire system and implement a countermeasure if necessary.
Need to Keep Your Business Protected?
Contact Us for the Business Security Your Company Needs
If you are a business owner who is interested in implementing Endpoint Protection to your current technological infrastructure, Blue Light IT can help you! We are highly experienced in this area of cyber security, along with every other aspect of digital security in Boca Raton and South Florida, and we would love to assist you in strengthening your business security.
Related Posts

Law Firms Beware: The Silent Ransom Group is Calling
read more
Slopsquatting: The AI Security Threat Every Development Team Must Address
read more