Almost everything is automated and accessible online, cyber attacks have become a great concern for individuals and businesses alike. Cyber criminals are becoming more advanced in their tactics, constantly developing new means to steal sensitive information from unsuspecting victims. From phishing scams to malware attacks, the types of cyber threats are numerous and continually evolving.
To stay protected against these threats, it’s essential to be aware of the various types of cyber attacks that exist and how to safeguard your data effectively.
Protecting yourself from cyberattacks isn’t just a smart choice – it’s critical. With that in mind, we’ve put together an informative article to help you understand the different types of cyberattacks and provide practical tips on how to stay secure online.
Knowledge is your shield. Learn about common threats and effective defense strategies with our Boynton Beach cybersecurity services.
Need to Learn More How to Keep Your Business Protected?
Common Types of Cyber Attacks and Their Characteristics
The most common types of cyber attacks include phishing, malware, ransomware, and denial-of-service (DDoS) attacks. Phishing attacks involve the use of fraudulent emails or messages that trick users into clicking on a link or downloading an attachment containing malware. Malware is malicious software designed to harm computer systems by infecting them with viruses, worms or trojans.
Ransomware attacks involve locking down your device access until you pay a sum of money to regain control over it. For example, hackers can lock important files on your computer and threaten to delete them unless a certain amount of money gets paid. DDoS aims at overwhelming servers with large traffic often originating from botnets; this prevents legitimate users from accessing websites and rendering services inaccessible. Tools like ransomware remediation in Boynton Beach and firewalls can help fight against these attacks and safeguard you against future ones.
Each type comes with unique characteristics in their operations but are bound to inflict significant damage if left unchecked. The consequences could range from financial loss to reputation damage if sensitive information falls into the wrong hands – knowing how attackers operate sets you apart as it enables building effective cybersecurity protocols against different threats.
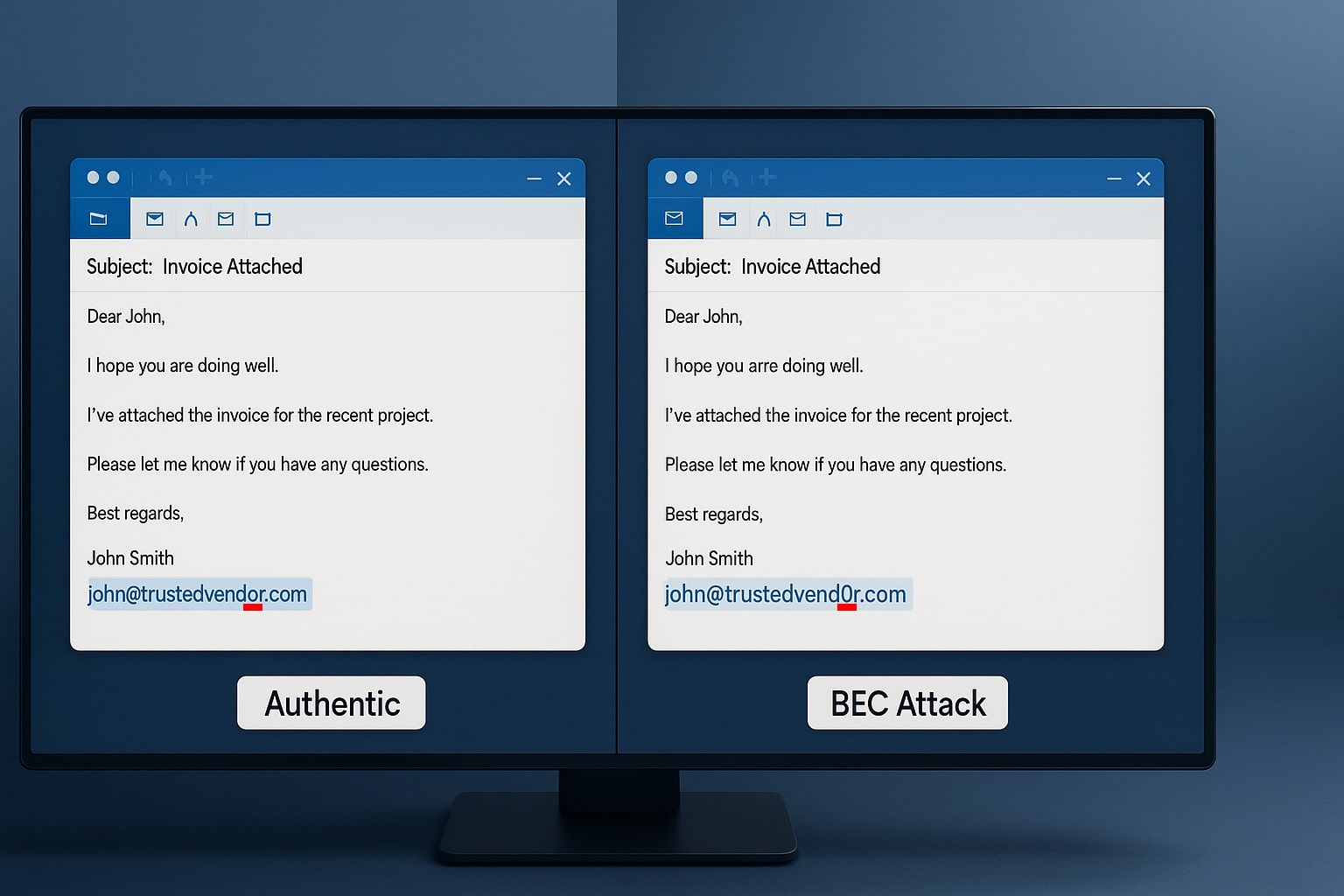
Phishing
Phishing is one of the most common types of cyber attacks. It involves fraudulent attempts to obtain sensitive information such as login credentials, credit card details or social security numbers. Attackers typically disguise themselves as trustworthy entities, often using email, phone calls or even SMS messages to trick individuals into divulging their personal information.
Phishing scams can be highly effective because attackers use techniques like social engineering to manipulate people’s emotions and provoke them into taking actions that they wouldn’t usually do under normal circumstances.
For example, an attacker might send an email claiming to be from a bank with a message stating that there has been suspicious activity on the victim’s account and prompt them to log in for further investigation by clicking on a link provided in the email which then leads them to a fake website designed purely for stealing login credentials.
Stay vigilant and protect yourself against potential phishing attacks by closely examining all emails and communication channels. Watch out for red flags like grammar mistakes or suspicious offers that seem too good to be true– they likely are! Refrain from clicking on any links included in questionable emails, instead go through your browser directly to ensure you’re only visiting official websites.
Need to Learn More How to Keep Your Business Protected?
Denial-of-Service Attacks (DoS)
One of the most common cyber attacks is a Denial-of-Service attack (DoS). In this type of attack, the attacker seeks to saturate or overwhelm a targeted system, such as a website or network, by flooding it with traffic. This traffic may come from multiple sources and can take various forms, such as packets that contain malformed data or requests that make unreasonable demands on the system’s resources.
The goal of a DoS attack is to disrupt normal operations for an extended period. This can cause significant inconvenience for users or businesses relying on the affected system and may result in loss of revenue and reputational damage.
Some criminals even use DoS attacks as part of larger extortion schemes in which they threaten further disruptions unless their demands are met.
To defend against DoS attacks, organizations should employ effective security measures such as firewalls and intrusion detection systems that monitor incoming traffic patterns continuously. They must also have backup strategies in place should their system become unavailable due to an attack. Finally, having protocols implemented for timely identification and response help mitigate impacts caused by successful cyberattacks like these ones.
Man-in-the-Middle Attacks (MITM)
Another common type of cyber attack to be aware of is the Man-in-the-middle attack (MITM). This technique involves an attacker intercepting communications between two parties, allowing them to eavesdrop or even alter the data being transmitted.
MITM attacks can occur in several ways, such as through public Wi-Fi networks where hackers can easily access unencrypted traffic. Attackers can also exploit vulnerabilities in web browsers and other software to inject themselves into otherwise secure communication channels. Once they have successfully intercepted information, attackers may use it for blackmail, identity theft, financial fraud or other malicious purposes.
To protect against MITM attacks, we recommend using encrypted connections whenever possible. This means avoiding public Wi-Fi or using a virtual private network (VPN) when necessary.
Regularly updating software and installing security patches can help mitigate risks from known vulnerabilities that attackers may seek to exploit. Additionally, users should remain vigilant against suspicious emails or messages which could serve as a gateway for an MITM attacker to gain access to personal information or sensitive data.
Malware
Malware, short for malicious software, is a type of cyber attack that involves the intentional creation and distribution of harmful computer programs.
Malware can take many forms, such as viruses, worms, trojans, spyware and ransomware. Once it infects a device or network, malware not only causes damage to the system but also exposes sensitive data to hackers.
There are various ways in which users may unwittingly download malware onto their devices – from clicking on suspicious links or attachments to downloading infected files disguised as legitimate ones. Some types of malware require manual installation by tricking users into granting permission while others self-install without user interaction. Malware infections often go undetected unless they start causing obvious issues with performance or security.
To protect against malware attacks requires ongoing awareness about best practices how to stay safe online including avoiding downloads from untrusted sources and relying on reputable antivirus software along with its ‘real-time’ feature enabled that checks every file downloaded from internet and alerts if finds anything suspicious.
Need to Learn More How to Keep Your Business Protected?
Stay Protected Against Cyberattacks
To sum up, cyberattacks have become a significant risk to personal and business security due to the increasing reliance on digital systems.
By being proactive with cybersecurity policies and protecting yourself to the best of your ability, you will be better equipped to ward off any attack attempts against you or your organization.
Want to properly protect your company against cybersecurity attacks? Build your digital fortress today with a Boynton Beach cybersecurity review.
Related Posts

Law Firms Beware: The Silent Ransom Group is Calling
read more
Slopsquatting: The AI Security Threat Every Development Team Must Address
read more